
Digital Evidence Investigator® gives investigators the ability to customize Search Profiles and determine exactly what and where you want to look for digital evidence. This is especially convenient..
Go to News article
With more than a dozen out-of-the-box Search Profiles inside Digital Evidence Investigator® (DEI) and all the ADF digital forensic and triage tools, the ADF Digital Forensic team has created software..
Go to News article
The investigation began when law enforcement officials received a report that images that were consistent with child pornography had been uploaded to a social media platform. The images were..
Go to News article
ADF is helping stop crimes against children by providing law enforcement with the right tools and training to combat internet crimes against children. As part of our mission to help fight child..
Go to News article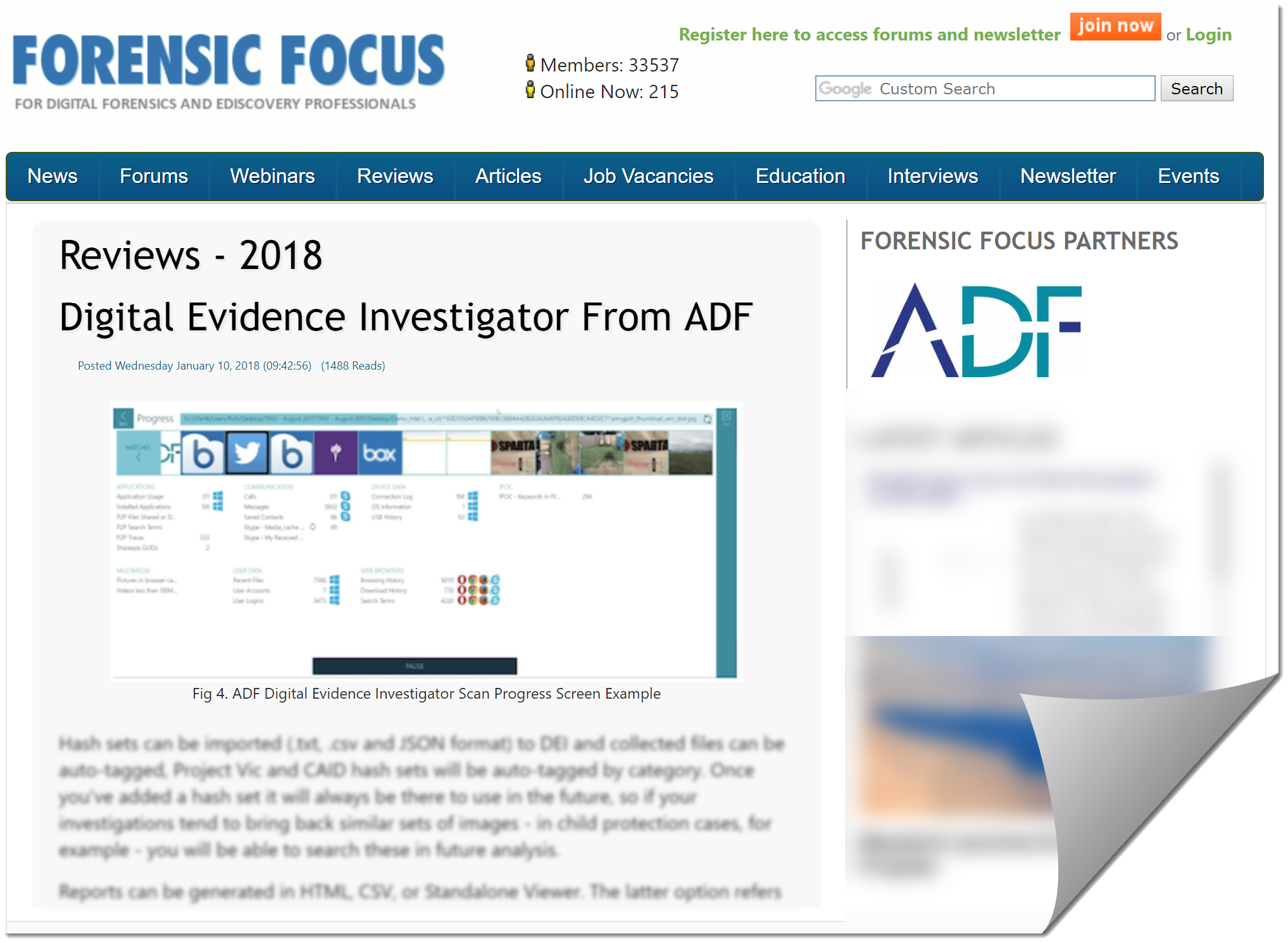
"In summary, I would say DEI is one of the more intuitive tools I've used, because it guides you through your investigation step by step and could easily be used without much training"...
Are you..
Go to News articleCopyright 2025 ADF Solutions, Inc. All Rights reserved.