
Welcome! You have a requirement or need and decided to evaluate one of the ADF products for your computer forensic, mobile forensic, or triage workflows. You have observed the videos and have most..
Go to News article
Investigating crimes against children has been at the forefront of law enforcement’s initiatives to dedicate the specialized manpower and equipment in order to battle this issue. It is not an easy..
Go to News article
In this 3-minute "How To" video, you'll learn the benefits of having a digital forensic triage process that works from field to lab. Using ADF digital forensic tools, examiners can prepare field..
Go to News article
The Encrypt backup feature in iTunes locks and encodes your information. In this short How To video, Director of Training, Rich Frawley shows investigators how to remove the known iTunes backup..
Go to News article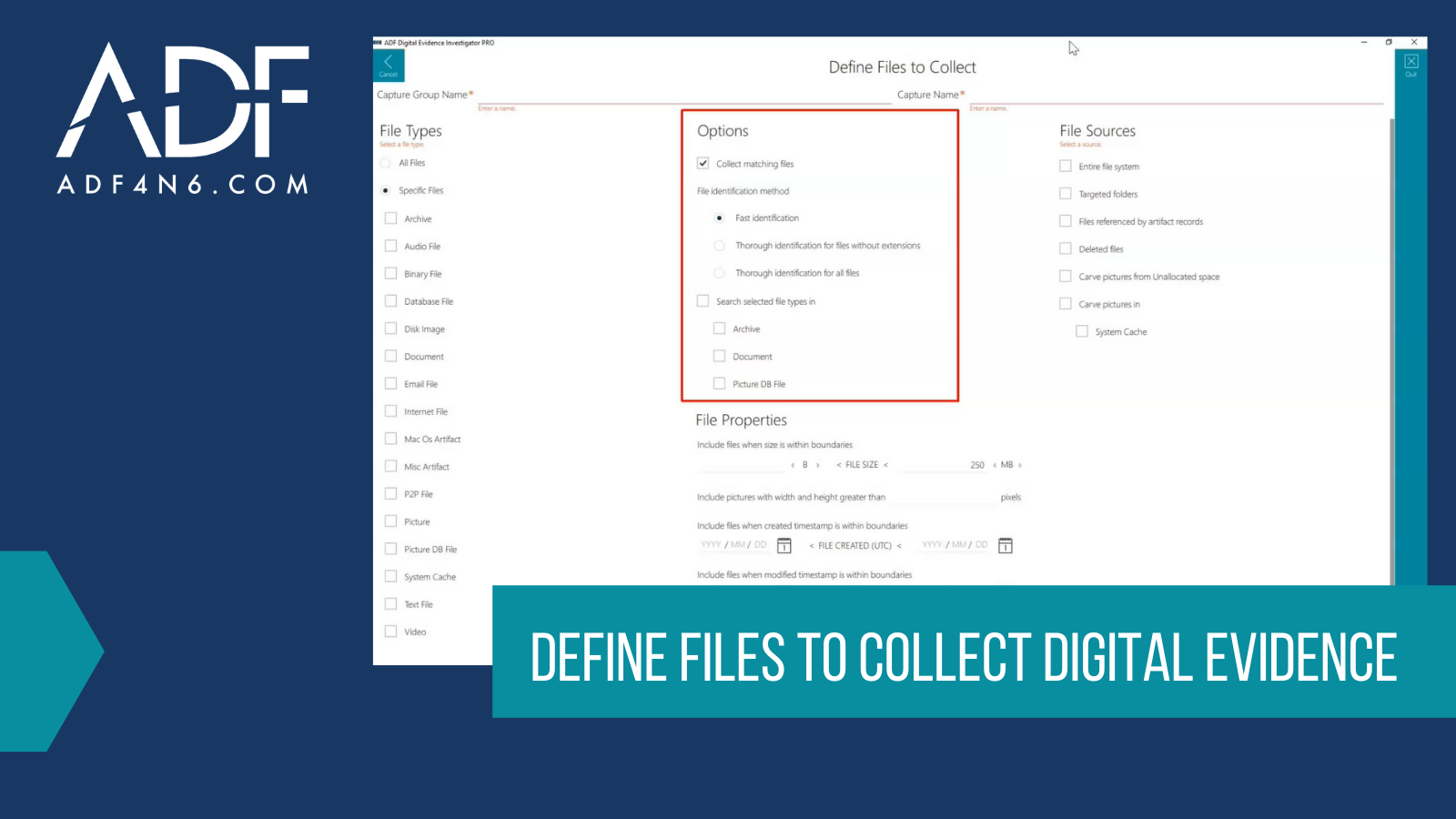
When collecting digital evidence, speed is often the name of the game, such as when you are serving a search warrant, dealing with a mass casualty incident, working a consent search, or trying to..
Go to News article
Getting ready to work off site, out of the lab, out of your office, and in someone else's domain is never an easy task. Whether it's a search warrant, in a client's office, suspect's residence, or..
Go to News articleCopyright 2025 ADF Solutions, Inc. All Rights reserved.