
ADF's Quick-Saved Credentials profile is a powerful profile that extracts the usernames and passwords from Web Browsers and is built so it will not trigger antivirus applications when attempting to..
Go to News article
The ADF Solutions suite of products are designed to get you to the relevant information in your digital forensic investigation, in a short amount of time so that decisions can be made. We at ADF..
Go to News article
There are many ways to learn digital forensics. From Certified Training to short How-To videos designed to teach you skills in just a few minutes. One of our favorite forms of learning, however, is..
Go to News article
In this 3-minute "How To" video, you'll learn the benefits of having a digital forensic triage process that works from field to lab. Using ADF digital forensic tools, examiners can prepare field..
Go to News article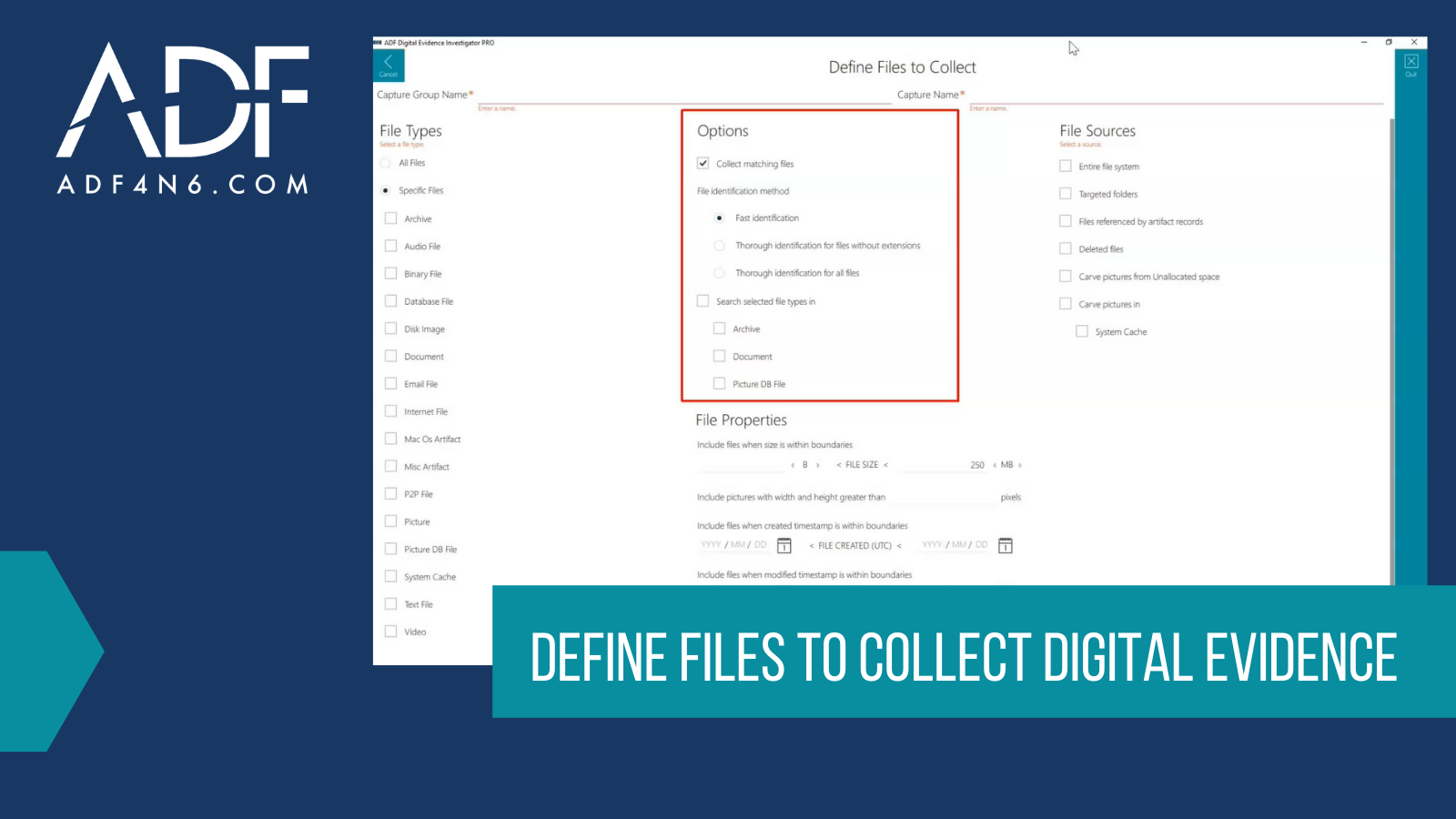
When collecting digital evidence, speed is often the name of the game, such as when you are serving a search warrant, dealing with a mass casualty incident, working a consent search, or trying to..
Go to News article
Copyright 2025 ADF Solutions, Inc. All Rights reserved.