
During a criminal investigation, prioritizing the evidence is paramount to your success as an investigator. Filtering what is critical to the case and what isn't is the difference between the success..
Go to News article
Within ADF software and forensic triage products, including Digital Evidence Investigator, Triage-Investigator, or Triage-G2, an investigator can quickly find Dark Web traces. This can be done in..
Go to News article
The Encrypt backup feature in iTunes locks and encodes your information. In this short How To video, Director of Training, Rich Frawley shows investigators how to remove the known iTunes backup..
Go to News article
Investigators can now scan all available Mac computers (including macs with T2 or M1 chips) with all types of encryption and virtual drives by running a remote agent that communicates with the..
Go to News article
Regular Expressions - (also known as "regex") are special strings representing a pattern to be matched in a search operation and they can be particularly useful in mobile and computer forensics..
Go to News article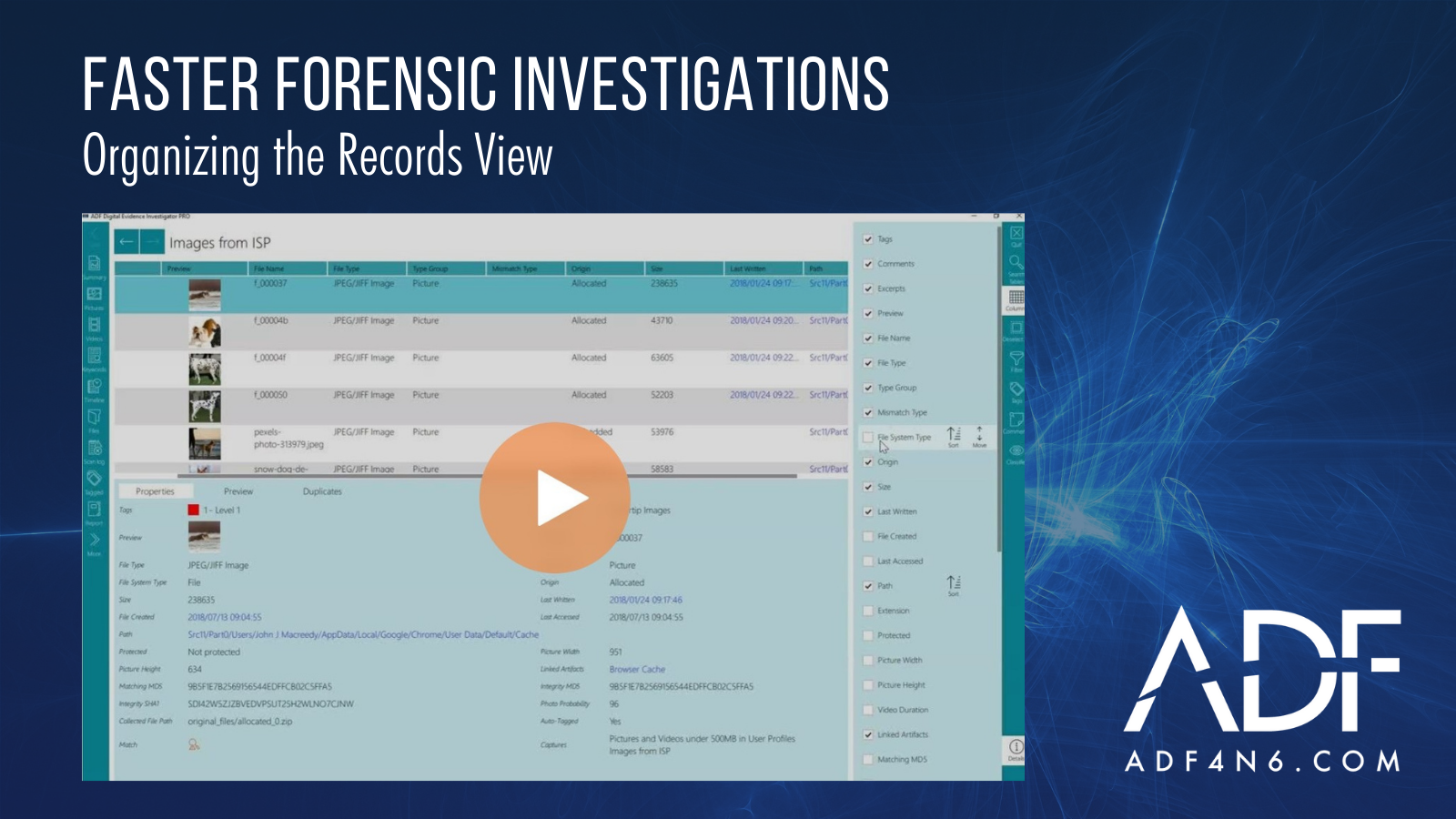
ADF digital forensic software is known for rapid file and artifact collection but we're also widely respected for our seamless user interface. No matter whether you are using Mobile Device..
Go to News articleCopyright 2025 ADF Solutions, Inc. All Rights reserved.